5 simple checks to spot a phishing email
This is a subtitle for your new post
It is getting harder to spot a phishing email as the fraudsters are improving their techniques and tactics to get through spam filters and to get past even the most tech-savvy of end users.
We've put together a guide of the 5 checks you can take to try and spot the good emails from the bad ones.
Check 1 – Try to confirm the sender.
Does the Display Name, the forename & surname of the sender match their email address?
In Outlook this can usually be found next to the sender’s name. If they don’t match, it’s likely to be a suspicious email.
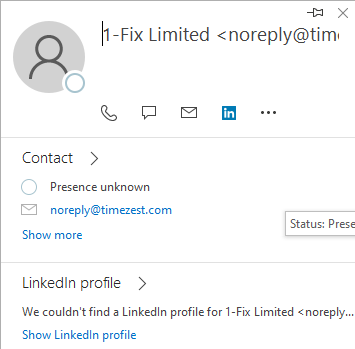
If the email is not displayed next to the sender’s name, hover the mouse over the name and wait for the contact card (shown below) to appear. The contact card will show useful information when trying to confirm the sender, such as social links like LinkedIn to help confirm their identity. If you know their contact card usually displays their LinkedIn but is not displayed here, then it may be a suspicious email.
This applies to anything you may notice as out of place in the contact card. Including their profile picture if they have set one.
Check 2 – Is the Email Expected?
It may seem obvious, but did you expect the email? If the email was unexpected it may be a sign that it is suspicious and to take a little extra caution. Run through the other checks to try and confirm if the email is safe. You may even wish to contact the company using a known trusted contact (if available) to check the details of the email.
Never use contact information given in an email that you are concerned may be unsafe. Use Google or a known and trusted contact to check. Some questions to ask if you do contact the company can include: “Does a John Smith work for your company?” or “Did your company or colleague send an email regarding X, Y, Z?”.
If the company say there is no person here by that name or we did not send any email regarding X, Y, Z then treat the email as suspicious.
Check 3 – Spoofing, language, and tone.
If the sender’s name and email match it still may not be trustworthy, this is due to “spoofing”. Spoofing is a fraudulent act in which an email from an unknown source is disguised as being from a known source and trusted by the recipient. The goal of this is usually to get people to share their personal data or perform an action on behalf of the spoofer. The spoofer will often take time and try to build trust with their target, thus helping them obtain sensitive data more easily.
If you think the email has been sent by a spoofer check the language and tone of the email. If you know your manager signs their emails off in a particular way and this sign off is missing this may be a sign it is not safe or trusted. If the email uses words or phrases you know they are not likely to use, if there’s uncommon spelling mistakes, or the tone feels strange to you these are all signs the email may not be safe.
Other things to look out for include: is the company signature missing? Do they usually address the email by name, but the email only addresses as Dear Sir/Madam? Are there strange gaps between paragraphs or sentences? All of these may also be signs that the email is not safe.
Check 4 – Links & Logos
If the email contains a link or a logo you can check to see if these are legitimate with some quick steps.
For logos, check if the logo is distorted. Does the logo match the current logo of the company? A quick google search for the company name or logo can reveal these discrepancies and help you decide if the email may be suspicious. You can also use this handy tool to check a company’s current logo https://clearbit.com/logo
Simply type in the company name and check the logo matches the one in the email. If they do not match, don’t trust it and take extra caution. If the logo looks correct check the links using the following steps.
To check if a link is suspicious, hover over it (do not click) and look in the bottom left corner or in the pop-up that appears. This shows the true destination and where the link would take you if clicked.
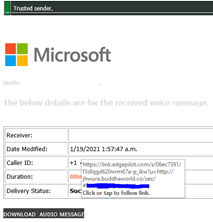
In this example below the logo claims the email is from Microsoft and the banner suggests it’s a Trusted Sender. When hovering over the button to Download audio message the true website is revealed. This link points to a site called jhwura.buddhaworld.co whereas a legitimate Microsoft site would usually be Microsoft.com so we can conclude this email is suspicious.
Check 5 – Your IT Department
If you’ve tried all of the steps above to determine for yourself if the email is safe or suspicious but cannot be sure or would like a second opinion, refer to your IT department to check. Your IT team will have some more tools at their disposal to check the email and even block the sender if you do not wish to receive email from them and are being repeatedly targeted.
There may be a specific way your IT team would like the email sent to them and may include a phishing report button or simply attaching the message as an attachment to a new email. In any case, your IT team will be able to advise you on how best to send the email in to them to be able to check and confirm if the email is safe.
If you have any questions about how 1-Fix can help protect your business, please comment below or get in touch!
Join Our Mailing List
All sign-ups are handled inline with our privacy policy and can unsubscribe at any time.